Intro
Azure Key Vault is a powerful tool that allows developers to securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets. However, one challenge that frequently arises is managing the expiration of these secrets. In this blog post, we will discuss how to set expiration dates for secrets and how to monitor these dates.
Azure Key Vault integration with Azure Event Grid enables user notification when the status of a secret stored in a key vault has changed. In the past it was only possible to have event grid and Azure automation accounts as destinations. These services are not as simple to setup and requires custom logic to handle the event.
Microsoft announced that Azure Monitor Alerts integration with Event Grid for Azure Key Vault system events is in public preview (still the case at the time of writing).
Public Preview: Azure Monitor Alerts integration with Event Grid fo…
By leveraging the features and seamless integration of Azure monitor we can seamlessly alert on the event that Azure Key vault emits.
The below steps will guide you to configuring this manually. If you prefer to use infrastructure as code templates. You can find them at the end of this article. IaC Templates
Setting Expiration Dates for Secrets
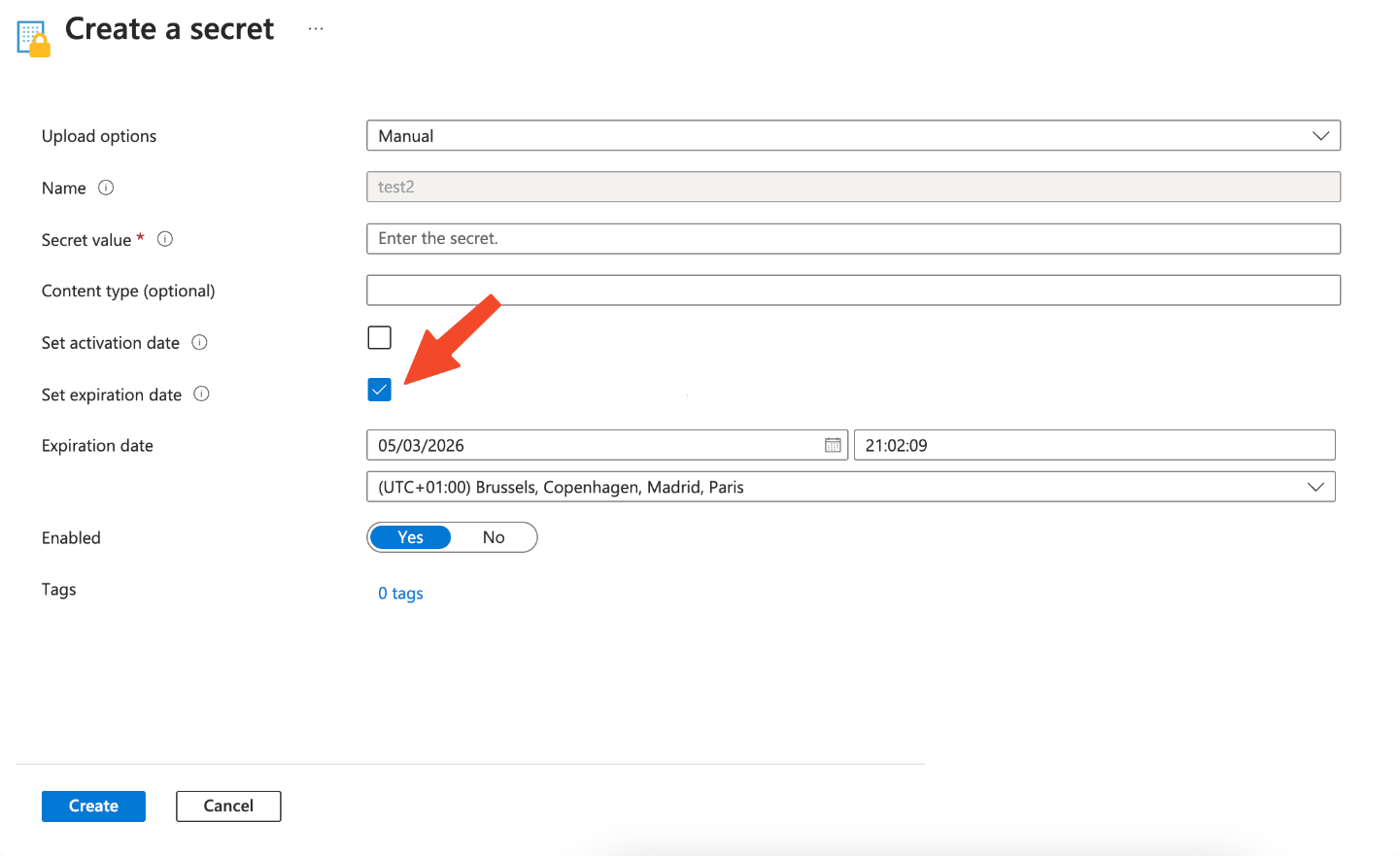
When creating a secret in Azure Key Vault, it’s important to set an expiration date. This helps to ensure that secrets are not used beyond their intended lifespan, adding an extra layer of security. To set an expiration date, you simply need to provide a date and time in the ‘Expires’ field when creating or updating a secret. Keep in mind that the date is in UTC format.Bonus: You can also leverage this Azure Policy to enforce the presence of expiration dates on every secret.
Create an action group
In order to create alerts for monitoring, you would first need to create an action group. An action group in Azure is a collection of notification preferences defined by the user. It is a reusable set of actions that can be used across multiple alerts. Once defined, the action group can be invoked from anywhere within Azure Monitor, and each action group can have as many as one thousand actions.
- Navigate to your resource group
- Click “Alerts”
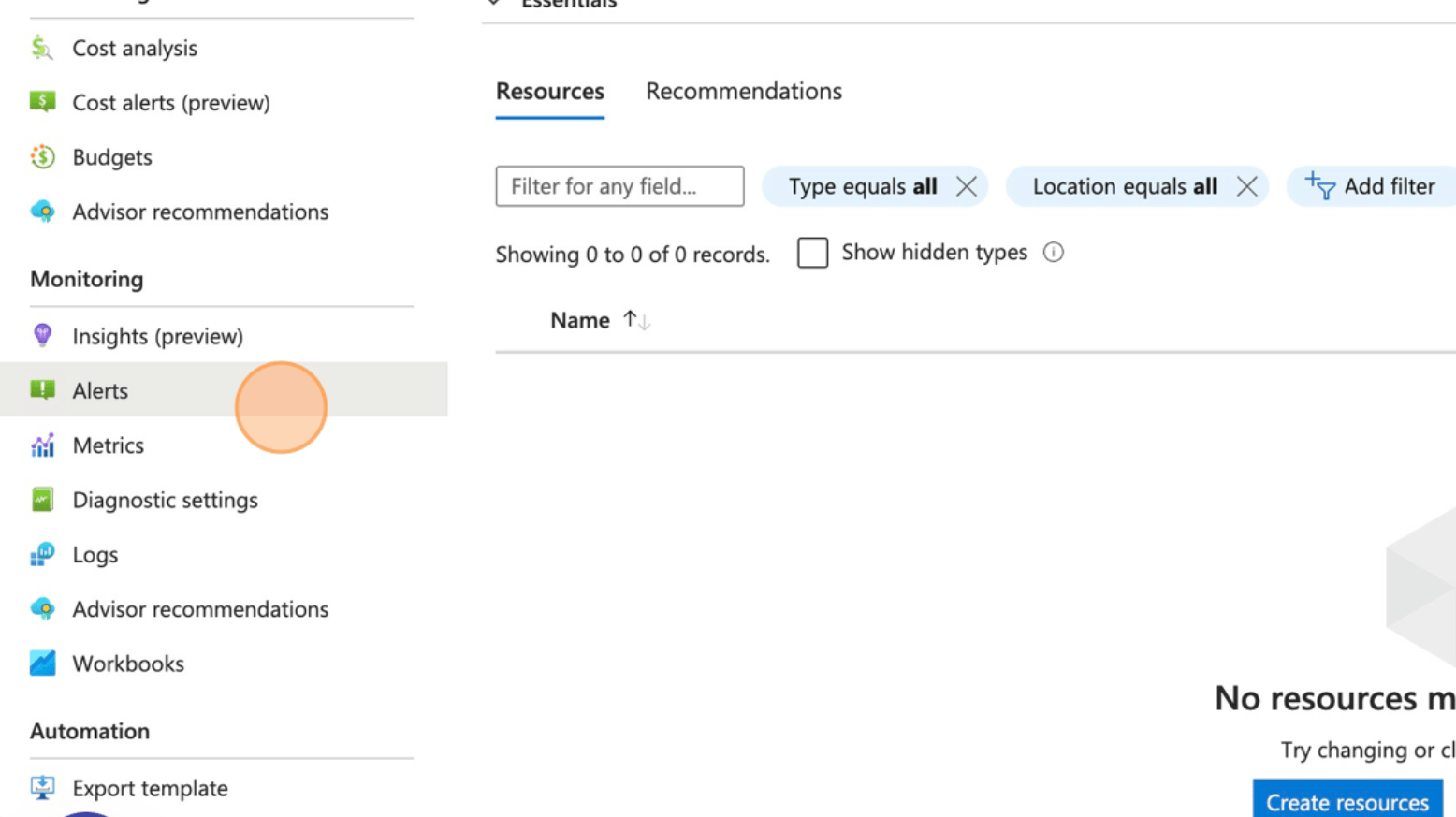
- Click Create and then action group.
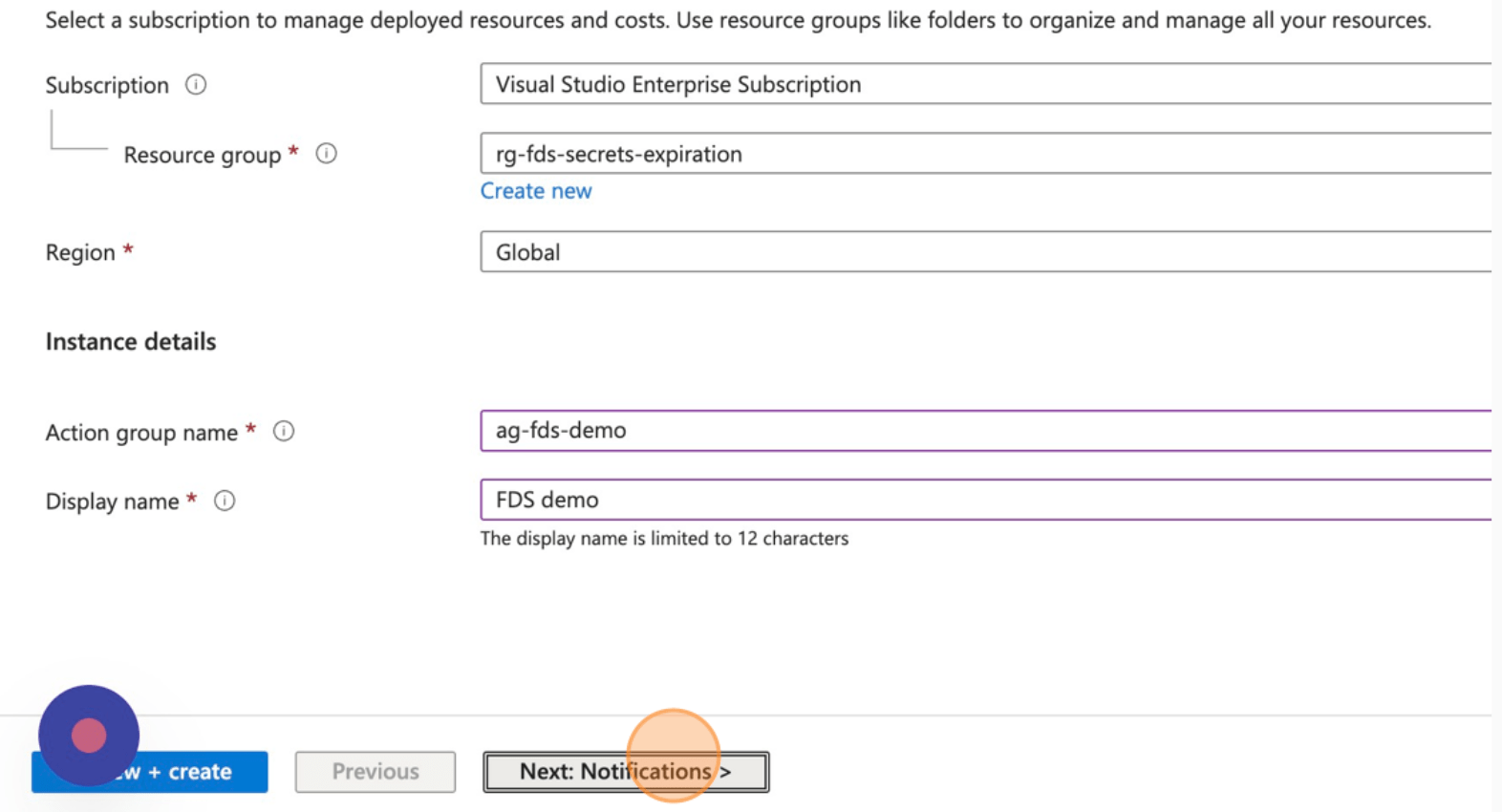
- Provide all requested information.
- Click “Next: Notifications”
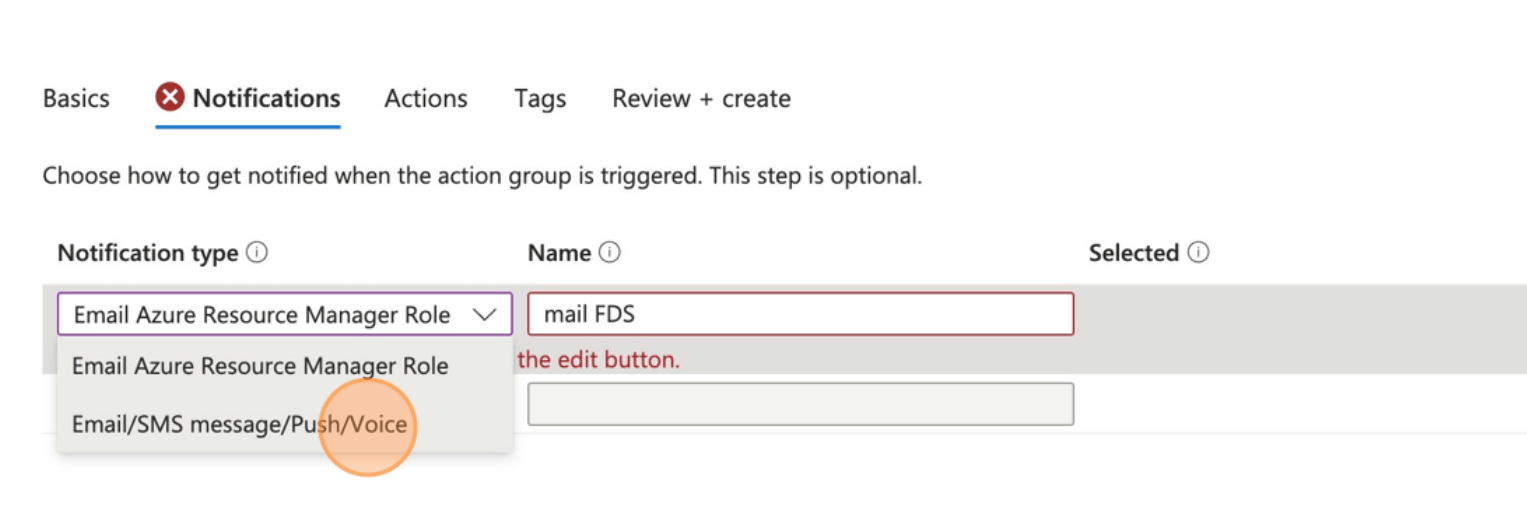
- Configure all the notification types you need.
- Create the action group.
Monitoring Secret Expiration Dates
It’s not enough to just set an expiration date, you also need to monitor it. Manually checking the expiration date of each secret can be error prone, especially in larger systems. Fortunately, Azure provides tools that can help. By using Azure Monitor and Azure Event Grid, you can set up alerts to notify you when a secret is nearing its expiration date. This allows you to take action before the secret expires.
- Go to your key vault
- Click “Events”
- Click here.
- Click all the events you want to be notified on. I’ve selected everything except for the “newVersionCreated” options. I don’ care about new versions.
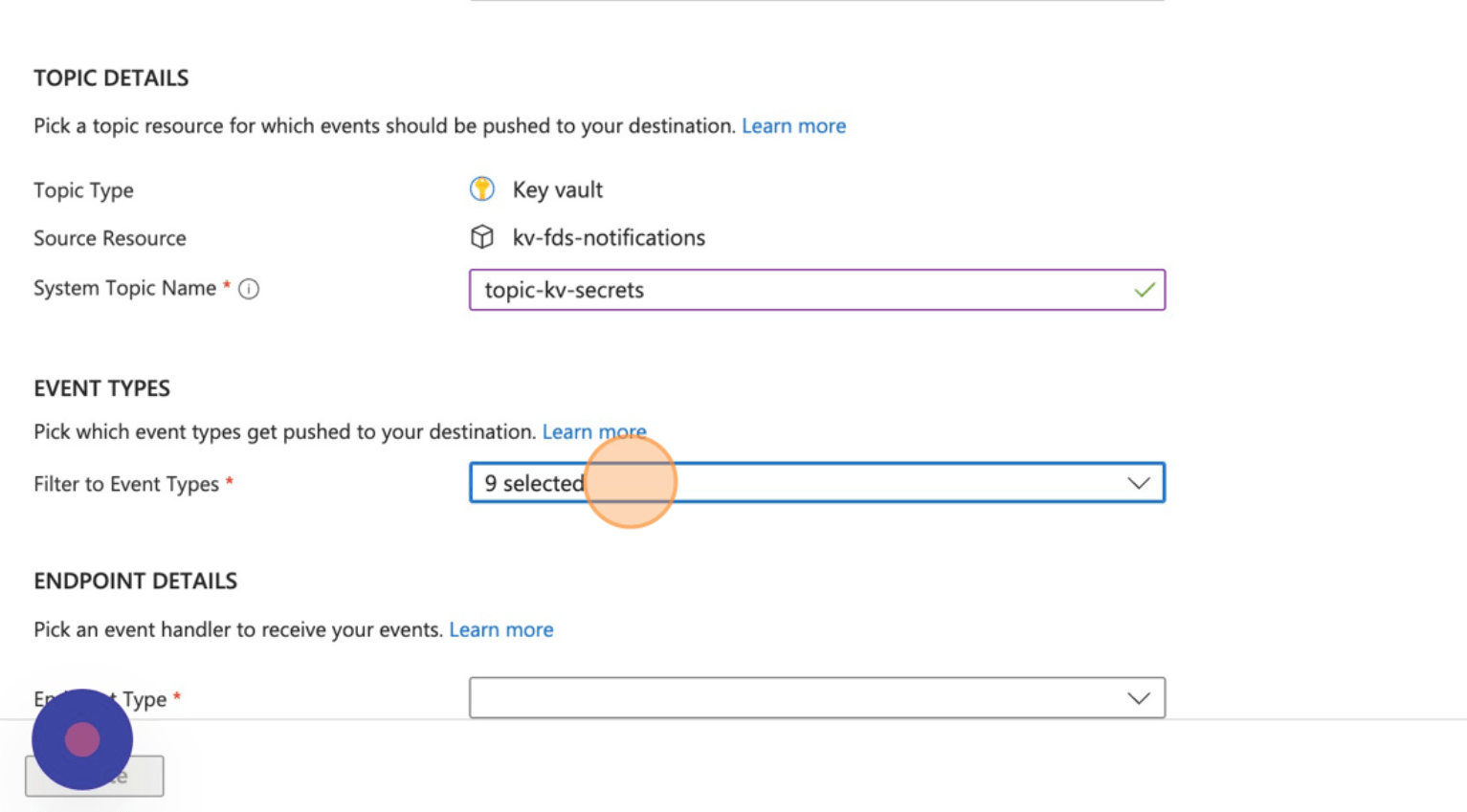
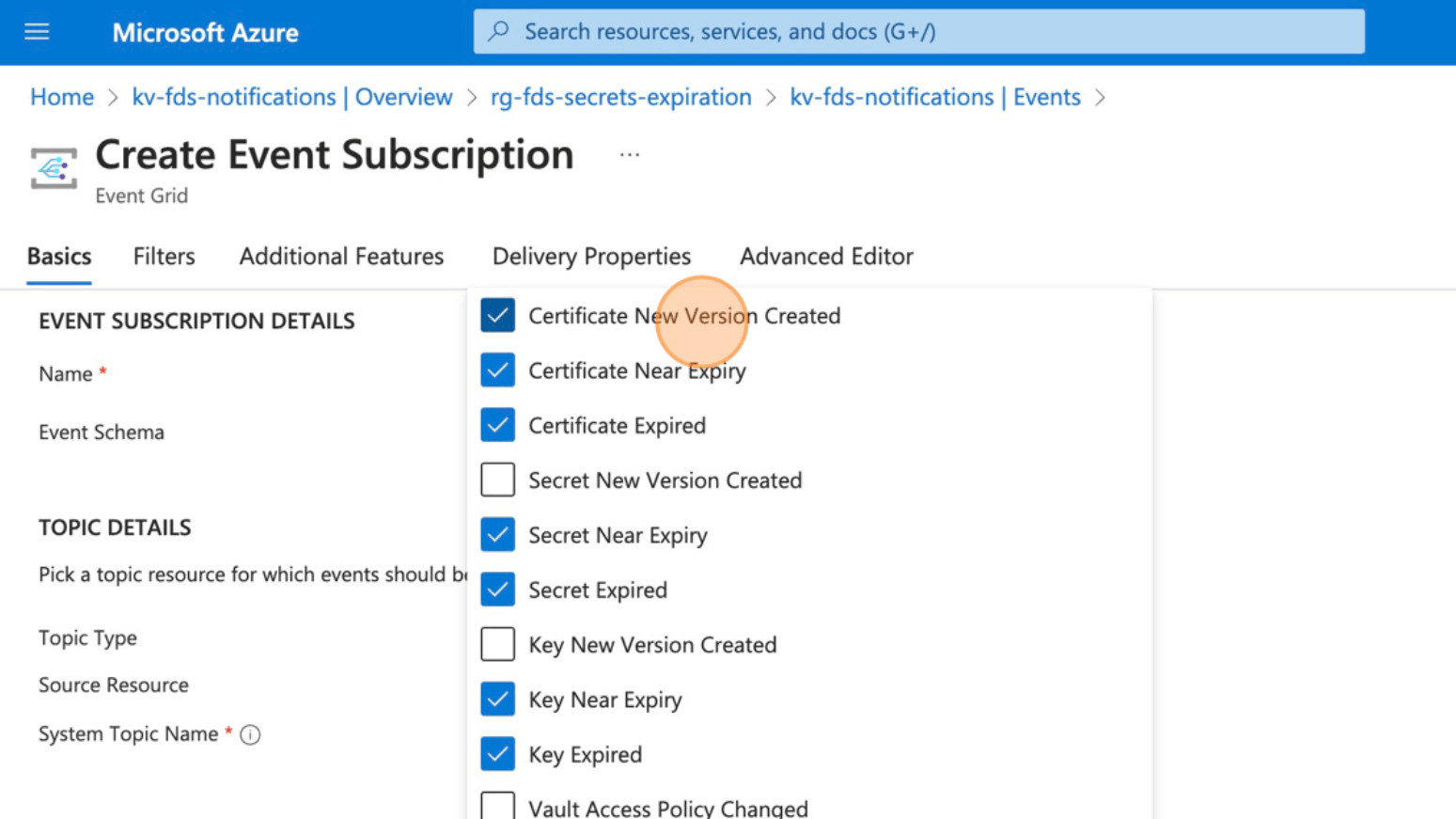
Note the events Microsoft.KeyVault.SecretNearExpiry & Microsoft.KeyVault.CertificateNearExpiry are triggered when the current version of a secret/certificate is about to expire. The event is triggered 30 days before the expiration date. This is not configurable.
- Click “Endpoint Type”
- Click Azure monitor alert.
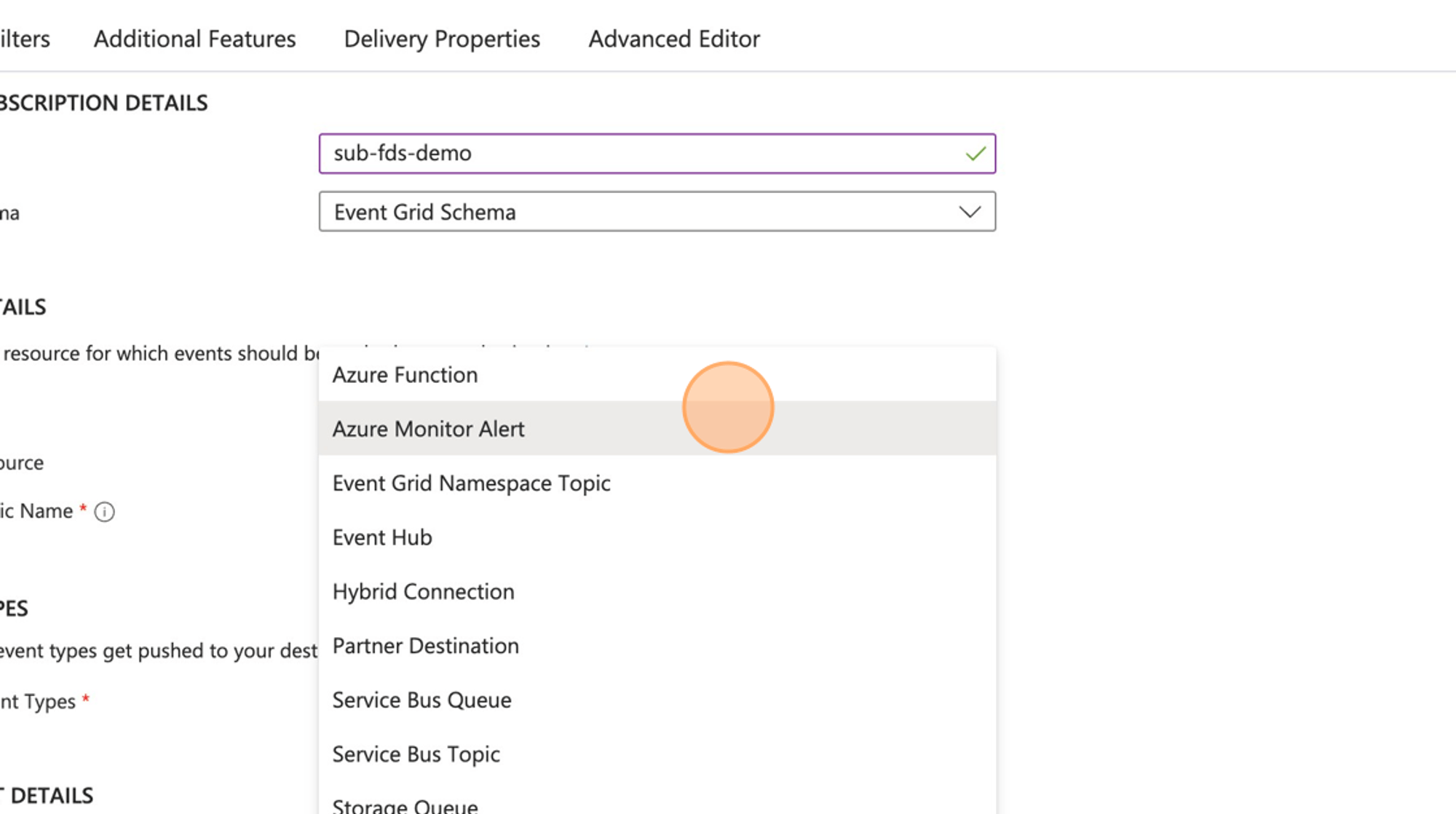
- Click “Configure an endpoint”
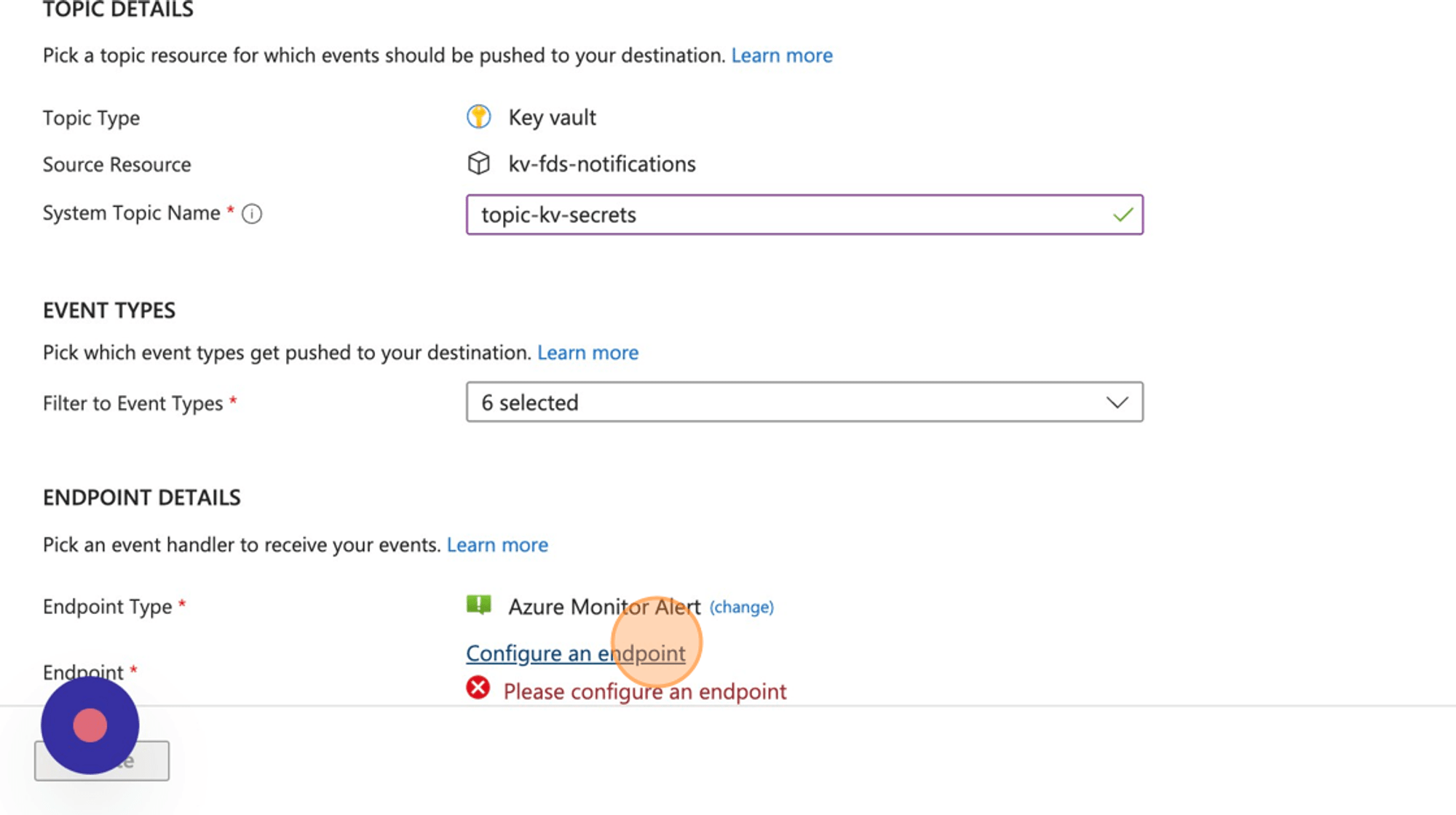
- Select the action group we created in the previous step.
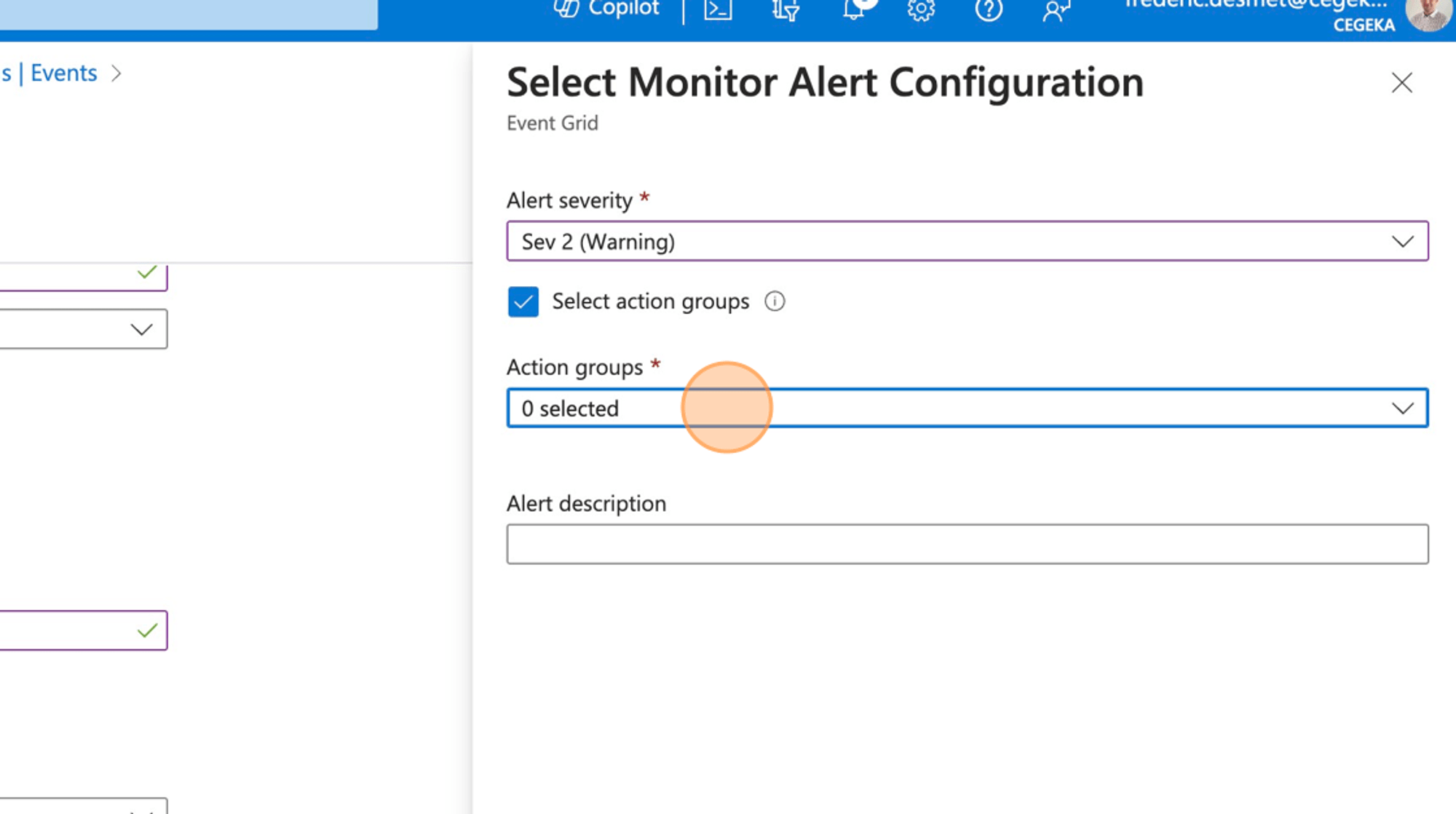
- Click create.
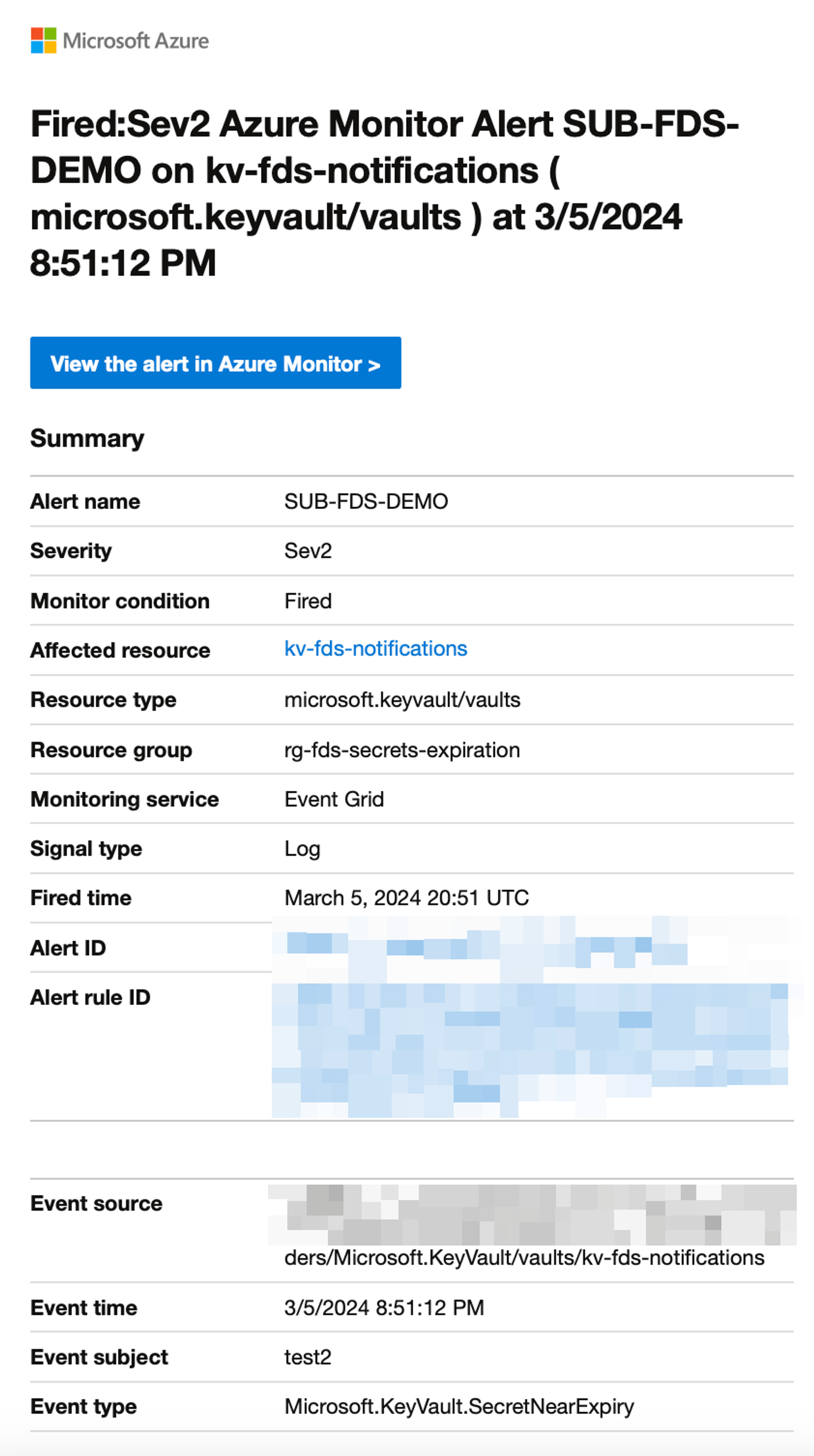
Example alert
In our example, we’ve set up an alert that sends an email notification 30 days before a secret is due to expire. This gives our team enough time to review and renew the secret, ensuring our system continues to run smoothly without interruptions.
This image shows an example of an alert for an upcoming secret expiration date. It outlines the details of the alert, including its status, severity, and so on.
IaC Templates
In this GitHub gist you’ll find the templates to deploy this setup yourself via IaC.
Please note that we’re using a preview api version at the moment of writing this post. This is also the reason why I don’t provide the Terraform code to implement this.
Conclusion
Managing the expiration of secrets in Azure Key Vault is crucial to maintain the security and integrity of your applications. By setting expiration dates, monitoring them, and (eventually) automating renewals, you can ensure that your secrets are always up to date and secure. Remember, a secure application is a successful application.



